It is truly a fine honor to travel around the world to speak at conferences. As an international speaker it is especially exciting to travel from Sweden to Sydney as an invited speaker.
NDC Sydney https://ndcsydney.com/ is a conference from the company NDC conferences, and that means a grand event with a top-tier of international speakers, a fine venue stocked with food, drink, and with a strong sponsor lineup. This is a learning experience to be reckoned with, that stands out among conferences around the world.
I will strongly recommend it is a good investment in personal development to attend one of these conferences, should you have the opportunity to do so.

“NDC Sydney 2024 will be an in-person event, held 12-16 February 2024 at Hilton Sydney. It's a five-day event comprised of 2-days deep-dive workshops, followed by 3 conference days with multiple simultaneous tracks.”
At NDC Sydney, I will speak, be interviewed, and I will interview none other than Mads Torgersen on my talk-show #TheCloudShow. Hope to see you all there! Below my session topic for the event.
Cheers,
Magnus
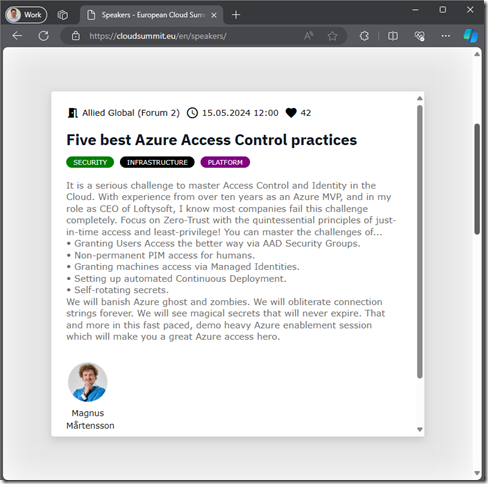
I will speak about how “Dev & Test Environments in Azure finally fast, cheap, and somewhat easy”!
This is a talk I really like, because I know very well how difficult it is to grasp and adopt environment automation in the cloud. I work with a lot of highly skilled and experienced IT-Pros and Devs, but maybe they have not got all that mileage in cloud yet, and with that comes a lerning curve for working with temporary environments in the cloud. When you need to do some testing for instance, you want to deploy the costly infrastructure to the cloud just-in-time and you want to remove it just after you finish your tests. At the same time you must know for sure that the environment you test on is configured exactly the same as the production target environment, otherwise what good is the test. Well, with automated testing (and development) environments, you can do all that. This is what my session explains and examplifies.
Here is my session description:
“If you are not using the cloud for Development and Test you are missing out – not really doing it right! Not all workloads belong in the cloud, but all development and test does for sure! While the cloud is becoming ever more empowering and capable, at the same time it can feel too advanced and too far away when you are developing and testing. Self-reported numbers put cloud resource consumption waste at so much as a third (1/3) of the monthly bill! Much of this waste may be attributed to failure to automate and to not optimizing working environments in the cloud.
Microsoft works diligently to make your Azure ascent exceedingly easy. With initiatives such as Azure Deployment Environments and Azure Developer CLI you the cloud user can enter one or a few commands on the line and hey-presto: You have a development environment running in the real Azure Cloud, just for you!
In this session we will look at two options from Microsoft in the paradigm of hands-free development and test environments as-a-service. Automation with Infrastructure as Code, extreme ease of use, built in compliance and security, and of course financial optimization are topics covered.
As a forward-thinking efficient developer, you need to be empowered with knowledge how to set up work in the Cloud, how to do your great job there, and how to optimize the spend your resource usage incurs! This session clears things up so that you can see the cloud despite all the fog. I also share my installation guide with links, including of course VS Code and Windows Terminal customization guidance. Enjoy!”






Comments are closed.